post exploitation: finding passwords in haystacks
Often while conducting an internal pentest you may gain access to a user machine through some vulnerability or more commonly via social engineering. Let’s say that you pop a shell, unprivileged, and incognito only finds unprivileged domain tokens. You could move onto another target or you can try some post exploitation reconnaissance. A commonly overlooked source of sensitive information is documents that are stored on the company servers as well as staff who think they know enough to start sharing folders with their peers and end up sharing the root of ‘C’. These can be a fantastic source of juicy info if you know how to index and then search through them effectively.
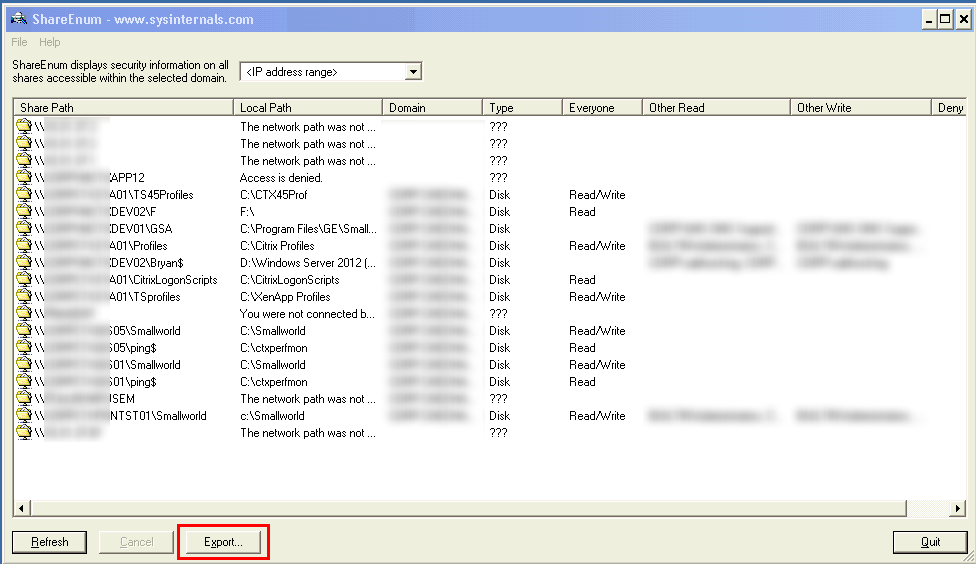
Firstly we need to see what shares your victim has access to. Nmap’s NSE will only get you so far but fortunately Microsoft has their own tool to do this for us, and best of all, it’s signed by Microsoft so using this is seldom an issue.
Grab ShareEnum from Sysinternals. It’s a self-contained executable that doesn’t require any installation. Wait for the vic to take lunch or head home, connect to his desktop and run the tool. If you don’t have his password yet, use the Metasploit Lockout Credential Keylogger. If you’re lucky enough, ShareEnum will get you all the shares for the entire domain otherwise just use the local subnets to search for the data stores. Make a note of the mapped drives and take note of the UNC paths; this will come in handy later.
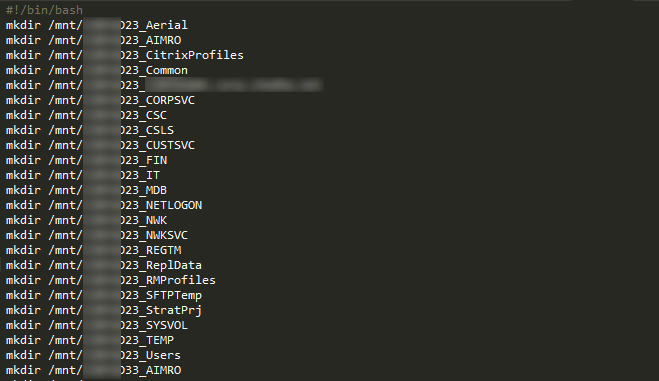
Once you’ve exported the data into a text file, use your text editor to get the share names and begin creating a mount script to mount them. Ensure that you mount them all under the same subfolder, e.g. /mnt or /media, so we can configure the indexer to only index these mounts and not waste time indexing your own drive. Run the script to create all the mount points.
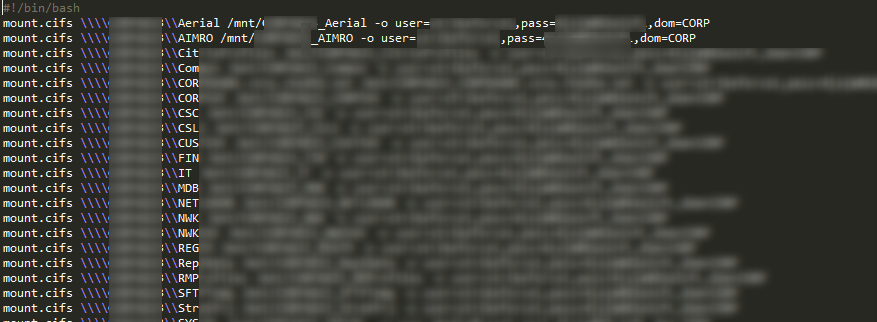
Once you’ve created a mount point for each of the shares, create a script to mount the shares and run it.
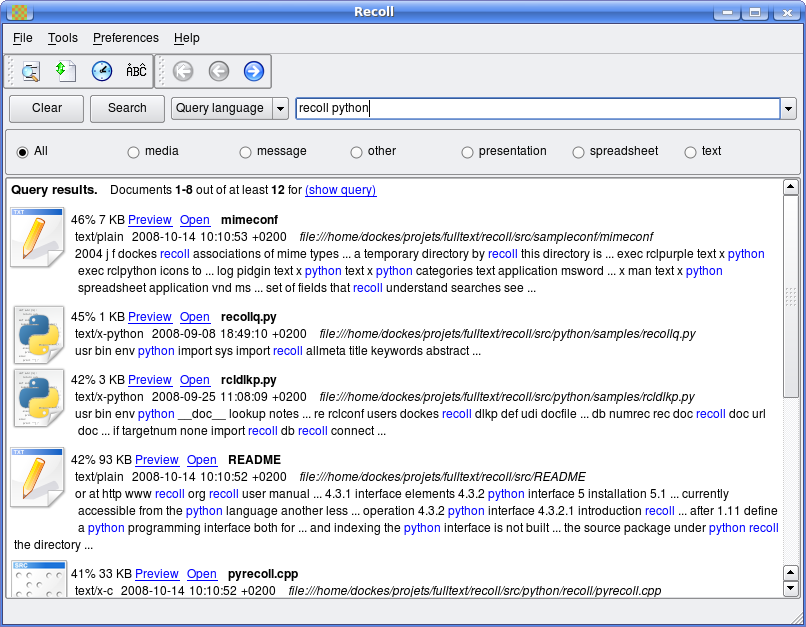
Now that the shares are mounted, the indexing tool needs to be installed and configured. A decent indexing tool that I would recommend is called Recoll. Recoll may already be installed in Kali. The benefit to using Recoll over some alternatives is that it can index the usual text and spreadsheet documents as well as inside ZIP file formats including the newer .DOCX, .XLSX and .PPTX. It also parses MIME, XML and PDF very well.
Installing recall on Kali or Ubuntu is pretty simple.
sudo apt-get install recoll
Once you have downloaded the tool, you will need to edit the config file which by default is stored at
~/.recoll/recoll.conf
I found these settings to be the best time/finding trade-off.
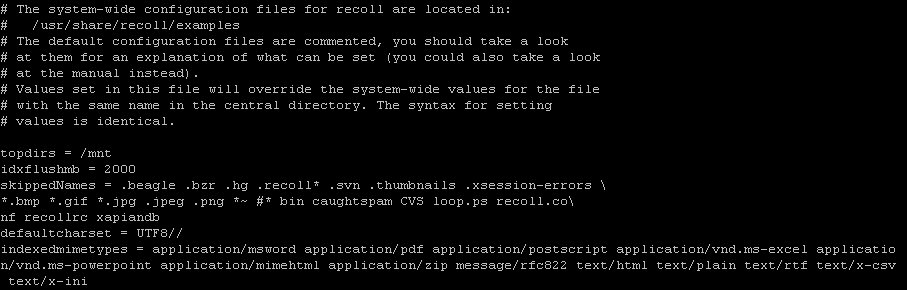
topdirs = path where you mounted the shares
idxflushmb = database store size before flush
skippedNames = files & extensions you don’t want indexed (filenames will still be shown, not contents)
indexedmimetypes = the file types that you want indexed
Once the config file is configured, pipe in the list of files you want indexed. Use a command such as
find /mnt –type f –print | recollindex –i
Once the files have been indexed, open up the Recoll GUI and start searching for keywords that will help get you some additional passwords. A list of keywords that worked well
credit card
ctrl alt del
domain\
id
ident
key
log in
log on
login
logon
net use
net user
pass
passphrase
passwd
password
pin
phrase
pw
pword
secret
ssid
un
uname
user
username
wireless
Here are a couple of screenshots from just a few shares that were available on this local subnet.
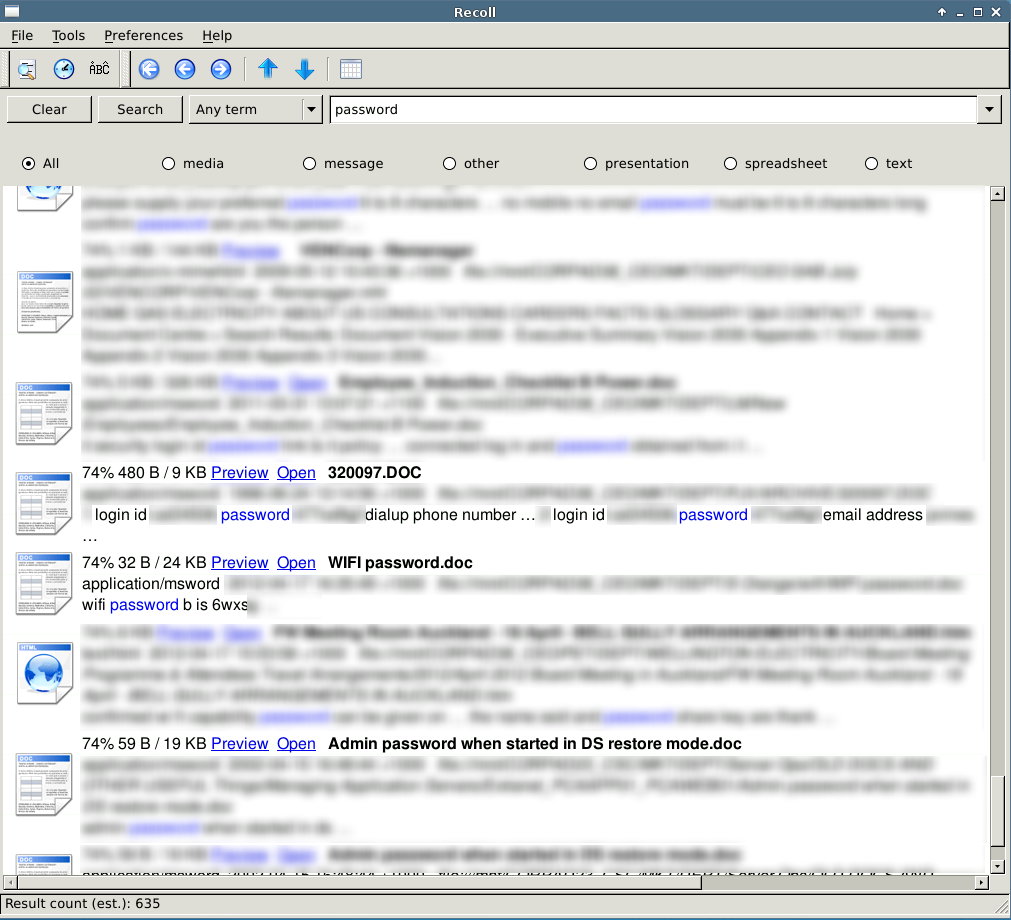
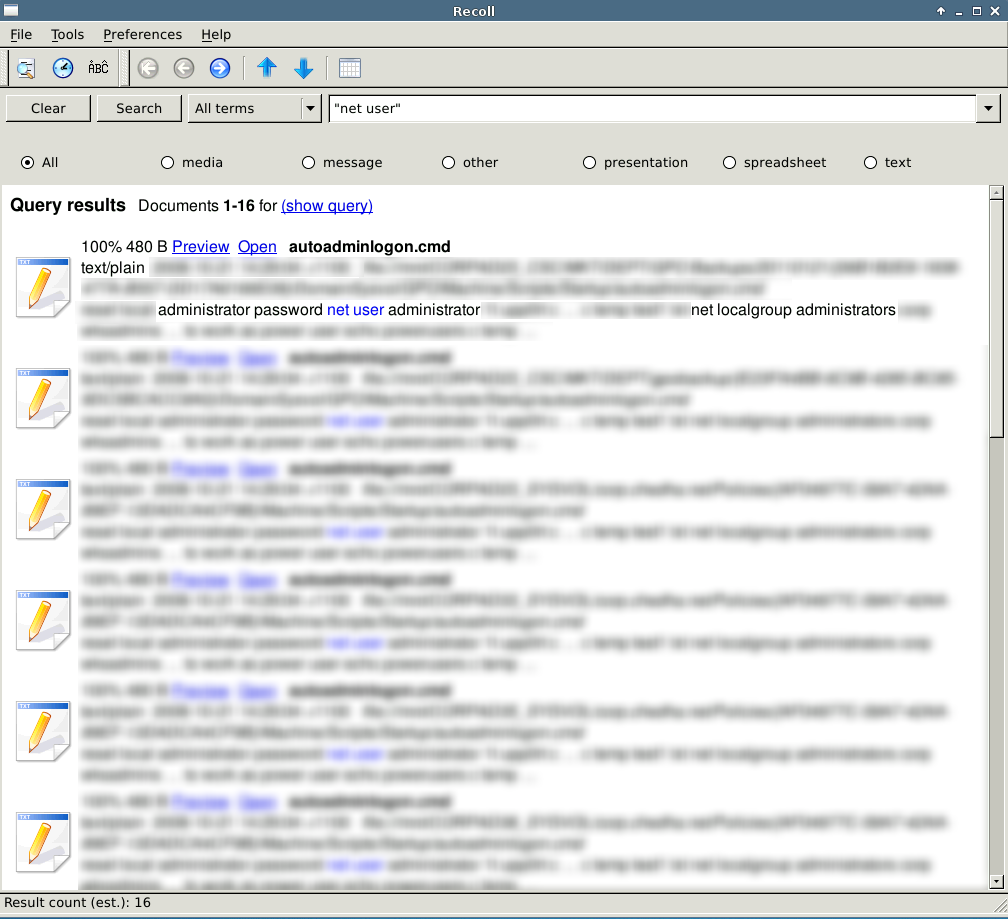
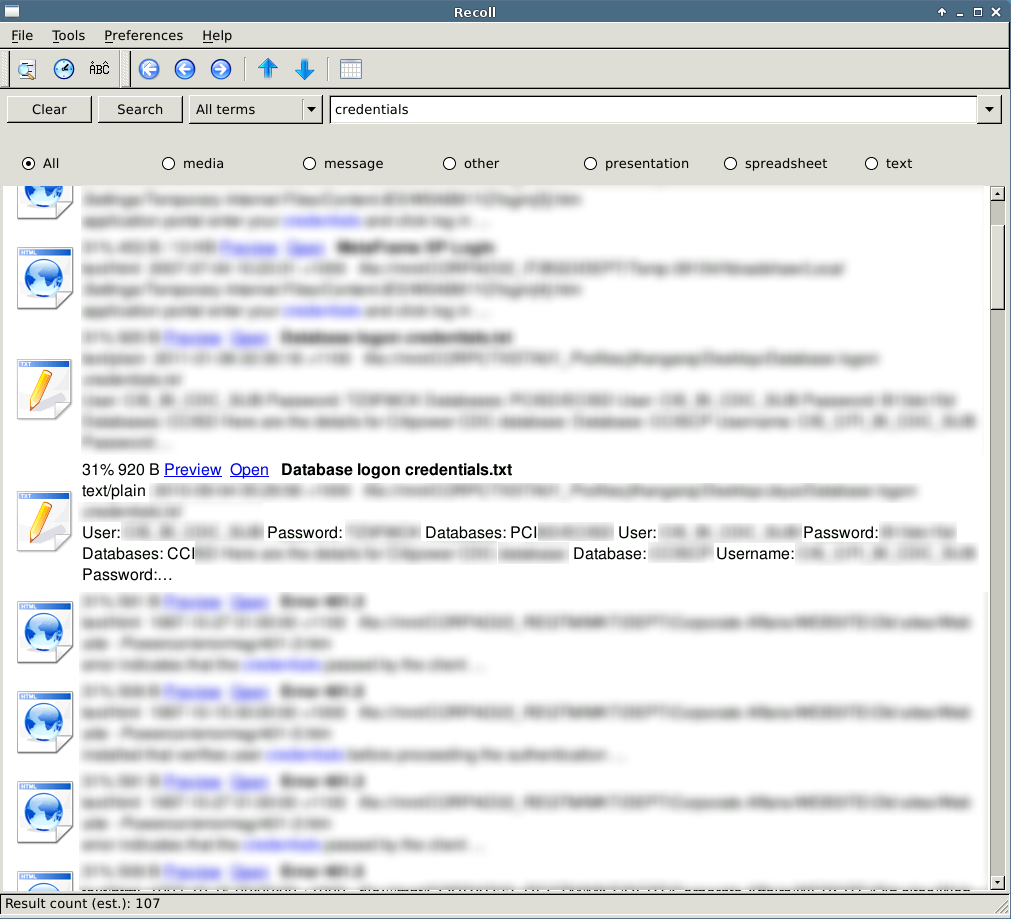
The keyword list is by no means comprehensive, however it should provide a solid foundation for a way of thinking about sensitive documents that are shared with everyone. As pentesters, we can use this information to increase our reach and impact on the client network. Knowing items such as the local administrator passwords and using them with PSEXEC can compromise the majority of machines on the network and the chances of now finding a domain administrator token on one of those boxes is going to increase.
Even the best training and policies are not going to stop certain system administrators from reusing passwords, so knowing some of these passwords can usually yield some interesting findings. Another high risk finding is the database credentials, which almost never get changed and often allow system commands to be executed.
Knowing how to find the sensitive information is a great skill to have in your arsenal and I hope this short post inspires you to become a better tester. The days of vulnerability scanners getting you root or system are numbered and exploiting the human weaknesses is becoming a necessity in modern networks.
Keep on sploiting,
norsec0de